In today’s fast-evolving digital payment ecosystem, security and efficiency are paramount. The EMV (Europay, Mastercard, and Visa) standard has emerged as the global benchmark for secure, chip-based payment transactions. Central to the EMV standard is the EMV Kernel, a critical EMV software component that ensures transactions are processed accurately, securely, and seamlessly.
At EazyPay Tech, we offer EMV Contact and Contactless Kernel solutions, seamlessly integrated with Terminal Applications and Payment Point of Sale (POS) terminals, ATMs. Our comprehensive EMV certification services are designed to support ATM and POS device manufacturers in achieving EMV Level 2 certification efficiently. Built to meet the latest global compliance standards, our certified EMV kernel solutions ensure secure and reliable transaction processing. With a strong international footprint across the USA, Malaysia, Thailand, Singapore, South Africa, the UAE, and more, we empower payment solution providers to accelerate time-to-market and stay ahead in the evolving payment ecosystem. Whether you’re developing new terminals or enhancing existing ones, EazyPay Tech is your trusted partner for end-to-end EMV kernel certification and integration.
This article provides a detailed overview of the EMV Kernel, its types, features, and applications across different payment environments.
What is an EMV Kernel?
An EMV Kernel is a software module embedded in payment terminals such as POS devices, ATMs, and SoftPOS solutions. It plays a pivotal role in facilitating communication between the EMV chip card and the payment terminal during a transaction. Acting as the intermediary, the kernel interprets the card’s data, applies stringent security protocols, and ensures compliance with EMV standards.
In simpler terms, the Kernel verifies the card’s authenticity, processes transaction requests, and communicates the payment data securely to the acquiring network. Without this software, payment terminals would be unable to process chip-based transactions efficiently and securely.
EMV Kernel Architecture
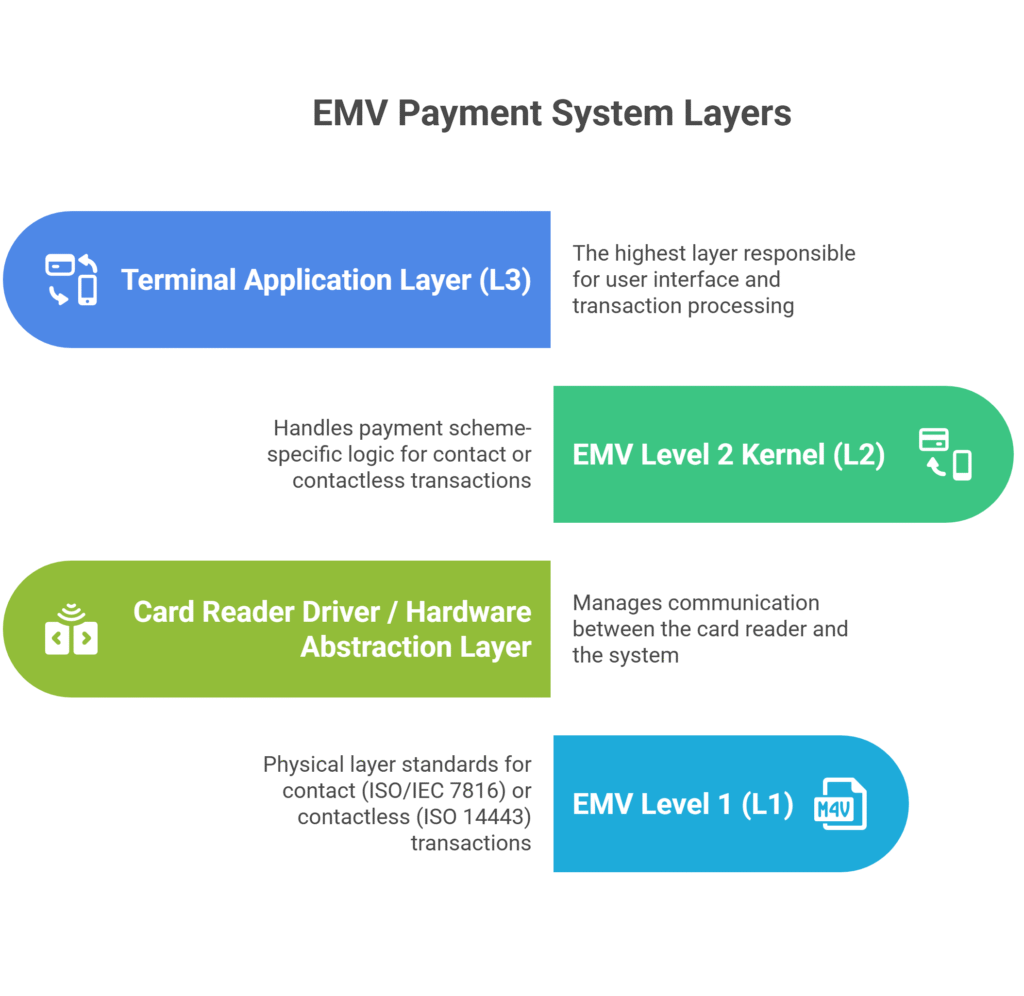
Terminal Application Layer (EMV Level 3 – L3)
- This is the topmost layer in the EMV stack and acts as the interface between the merchant or terminal and the end-user (cardholder).
- The Terminal Application controls the transaction flow, user interface (UI), and overall logic of a payment transaction.
- It initiates transactions, displays prompts, collects user input (e.g., PIN entry), and processes results returned from lower layers.
Responsibilities
- Transaction initiation and completion.
- Interaction with host/acquirer systems.
- Managing multi-application environments on a single terminal.
- Invoking EMV Kernel functions like Application Selection, Card Authentication, Risk Management, and Terminal Action Analysis.
- Formatting data for the receipt and transaction logs.
Example
When a card is inserted or tapped, the application layer initiates the transaction, communicates with the EMV kernel to process card data securely, and then completes the process by sending the transaction to the bank or acquirer.
EMV Level 2 Kernel (L2) – The Core of EMV Logic
- The EMV Kernel is the brain of EMV transaction processing. It interprets card data according to EMVCo specifications and manages the decision-making processes during a transaction.
- L2 is responsible for executing the EMV specifications (such as Application Selection, Offline Data Authentication, Cardholder Verification, Terminal Risk Management, and more).
- Each payment scheme (Visa, Mastercard, RuPay, etc.) may have its own certified version of the kernel.
Key Functions
- Application Selection – Identifying which application on the card to use.
- Card Authentication – Ensuring the card is genuine via methods like SDA, DDA, or CDA.
- Cardholder Verification – Determining how the cardholder’s identity should be verified (PIN, signature, etc.).
- Terminal Risk Management – Evaluating if the transaction should be processed online or offline.
- Transaction Authorization – Communicating with the card and host to approve or decline the transaction.
Contact vs Contactless
- The same principles apply, but contactless kernels are optimized for faster, “tap and go” experiences and must comply with specific contactless EMV profiles.
Card Reader Driver / Hardware Abstraction Layer (HAL)
Description
- This layer provides a bridge between the EMV Kernel and the physical hardware of the card reader.
- It abstracts the details of the hardware, offering a standardized interface to the upper layers.
- This allows the EMV Kernel to operate independently of the specific hardware configuration, making it portable across different devices.
Responsibilities
- Managing low-level operations like powering the card, data transmission, and reset handling.
- Supporting communication protocols (T=0, T=1 for contact; Type A/B for contactless).
- Detecting card presence and removal events.
- Interfacing with secure elements or SAMs (Secure Access Modules), if used.
Benefit
By separating hardware-specific logic from the EMV Kernel, developers can reuse the same EMV kernel on different terminal hardware platforms with minimal changes.
EMV Level 1 (L1) – The Physical and Communication Layer
- This is the foundational layer responsible for establishing and maintaining physical and electrical contact between the card and the terminal.
- It complies with international standards like ISO/IEC 7816 for contact cards and ISO/IEC 14443 for contactless cards.
Specifications
- Contact Cards:
- ISO/IEC 7816 defines the mechanical and electrical characteristics of the smartcard and its connector.
- It covers aspects such as voltage levels, timing constraints, and communication protocols.
- Contactless Cards:
- ISO/IEC 14443 defines the physical characteristics, RF interface, and data transmission protocols for proximity cards.
- It includes anti-collision mechanisms, command structures, and field strength parameters.
Responsibilities
- Powering up the card.
- Initializing communication with the card (ATR/ATS exchange).
- Exchanging APDU (Application Protocol Data Units) commands and responses.
- Ensuring compliance with timing and voltage tolerances.
Why Layered Architecture Matters
The layered architecture of the EMV system provides several key benefits:
- Modularity: Each layer is independent, making the system easier to develop, maintain, test, and certify.
- Interoperability: Adherence to global standards ensures terminals work with cards from different issuers worldwide.
- Security: EMV Kernel and Terminal Application layers work together to enforce strong cryptographic validation, minimizing fraud.
- Scalability: New hardware or card technologies can be integrated without rewriting entire systems. Only the abstraction layer might need updates.
Types of EMV Kernels
EMV technology has revolutionized the payments industry by enabling secure and efficient processing of transactions. Two primary types of EMV Kernels cater to different transaction scenarios: Contact EMV Kernel and Contactless EMV Kernel. Both types play essential roles, depending on the specific use case, environment, and user convenience.
EMV Contact Kernel
EMV Contact Kernels are utilized in transactions where the card is physically inserted into the payment terminal. These are primarily seen in chip-and-PIN or chip-and-signature transactions, where the card’s EMV chip establishes a physical connection with the terminal.
The Contact Kernel ensures a secure channel for data exchange, authenticating the transaction and preventing fraud. By requiring the card to make direct contact with the terminal, it provides high reliability and robust security, making it ideal for scenarios where secure, authenticated payments are non-negotiable.
Applications of EMV Contact Kernel
- Retail Environments: Contact Kernels are widely deployed in traditional retail settings where customers insert their cards into POS terminals to make purchases securely.
- Supermarkets and departmental stores use contact kernels to handle transactions for large volumes of customers.
- The physical connection ensures a high degree of security in these environments.
- ATMs: ATMs heavily rely on EMV Contact Kernels for card insertion and authentication, ensuring secure withdrawals, balance checks, and other banking services.
- ATM machines validate the cardholder’s PIN, authenticate the card, and securely process transactions.
- This is particularly critical for sensitive transactions like cash withdrawals.
- Banking and Secure Transactions: Contact Kernels are ideal for high-value, security-critical environments like banking and financial services, where a physical connection minimizes the risk of fraud.
- Used in branches where security is non-negotiable for significant financial operations.
- Also applied in B2B payment solutions requiring authenticated payments.
Key Features of Contact Kernel
- Physical Connection: The card must be physically inserted into the payment terminal, ensuring a secure and direct interface. This physical connection enables the chip and terminal to exchange encrypted data securely.
- Enhanced Security: The physical connection minimizes vulnerabilities such as skimming and data interception, as the data is transmitted through a secure channel. This makes it highly effective in environments with a higher risk of fraud.
- Transaction Authentication: The kernel validates the cardholder’s credentials and ensures the transaction complies with EMV security protocols. This involves verifying the chip, PIN, and sometimes the cardholder’s signature.
- Reliability: Contact Kernels offer highly reliable processing, making them essential in high-stakes environments like ATMs and financial institutions. They ensure accurate data exchange even in environments with potential signal interference.
EMV Contactless Kernel
EMV Contactless Kernels enable transactions without physical contact between the card and the terminal. Instead, the transaction is initiated when the card is tapped or waved near a terminal equipped with NFC (Near Field Communication) or RFID (Radio Frequency Identification) technology.
The Contactless Kernel facilitates fast, secure, and efficient payments, making it a preferred choice for environments where speed and convenience are critical. By leveraging secure short-range communication, contactless technology provides an enhanced customer experience without compromising transaction security.
Applications of EMV Contactless Kernel
- Public Transit Systems: Contactless Kernels are widely used in transit systems, where commuters tap their cards for quick entry and exit.
- Commuters save time during peak hours as they quickly pass through automated gates using tap-and-go technology.
- Contactless kernels enable seamless payment without the need for cash or ticketing machines.
- Quick-Service Restaurants (QSRs): In fast-paced environments such as quick-service restaurants, contactless payments allow customers to complete transactions quickly, reducing queue times and improving overall efficiency.
- Customers enjoy a hassle-free experience, enabling businesses to serve more patrons in less time.
- Major food chains leverage contactless kernels to meet the demand for fast, frictionless transactions.
- Retail Environments: Contactless payments are increasingly popular in retail settings, especially in high-traffic areas such as supermarkets, convenience stores, and shopping malls.
- Retailers use contactless technology to accelerate checkout lines and enhance the customer experience.
- Consumers prefer the convenience of tapping their cards for transactions under a certain limit, as it eliminates the need for PIN entry.
Key Features of Contactless Kernel
- NFC/RFID Technology: Contactless Kernels leverage NFC or RFID technology for short-range, secure communication between the card and the terminal. This technology ensures fast data transmission while adhering to EMV security standards.
- Speed and Efficiency: Contactless transactions are significantly faster than traditional methods, eliminating the need for card insertion or PIN entry for small transactions. This is particularly valuable in high-traffic environments where transaction speed is critical.
- Enhanced Convenience: The ‘tap-and-go’ experience enhances customer satisfaction by reducing wait times and providing a seamless checkout process.
- Secure Data Exchange: Despite the lack of physical contact, Contactless Kernels adhere to EMV security standards. Sensitive card information is encrypted during the transaction, reducing the risk of fraud.
- Adaptability: Contactless Kernels are compatible with mobile wallets and wearables, such as smartphones, smartwatches, and other NFC-enabled devices. This adaptability makes them ideal for modern digital payment ecosystems.
EMV Kernels: Ensuring Security and Compliance
Both Contact and Contactless EMV Kernels are designed to ensure transaction security and compliance with global EMV standards. These kernels incorporate several critical functions, including:
- Card Authentication: Verifies the card’s authenticity to prevent counterfeit fraud.
- In Contact Kernels, this involves validating the physical EMV chip.
- In Contactless Kernels, secure NFC-based authentication ensures integrity.
- Cardholder Verification: Validates the cardholder’s identity using PINs, signatures, or other authentication methods.
- For Contact Kernels, this often involves chip-and-PIN or chip-and-signature authentication.
- For Contactless Kernels, PIN entry may be required for higher-value transactions.
- Transaction Authorization: Ensures the transaction is authorized by the issuing bank or payment network. This step ensures sufficient funds and fraud checks are performed.
- Data Encryption: Protects sensitive payment data by encrypting it during transmission to prevent unauthorized access.
- Interoperability: EMV Kernels are designed to work seamlessly with cards and terminals from different issuers, ensuring global interoperability.
The implementation of EMV Kernels has significantly improved security, reliability, and efficiency within digital payment ecosystems. One of the key benefits is fraud reduction, as EMV technology drastically minimizes card-present fraud by authenticating cards and encrypting payment data. Additionally, EMV Kernels enable global standardization, ensuring compliance with international payment standards and facilitating seamless cross-border transactions. The technology also enhances user experience, particularly through contactless kernels, which provide fast and frictionless payment solutions to meet the needs of modern consumers. Moreover, EMV Kernels support emerging technologies, such as mobile payments and wearable devices, making them adaptable and future-ready for merchants and banks.
In a world increasingly reliant on secure, efficient payment solutions, EMV Kernels serve as the foundation of modern payment processing. Whether through physical contact or contactless methods, EMV Kernels ensure transactions are secure, reliable, and compliant with global standards.
The choice between EMV Contact and Contactless Kernels depends on the specific needs of the payment environment. Contact Kernels excel in high-security, high-value transactions, while Contactless Kernels prioritize speed and convenience for everyday payments.
As businesses and consumers continue to embrace digital payment solutions, the role of EMV Kernels will only grow in importance, driving innovation and security in the payment industry.
Stay Ahead in the Digital Payment Revolution. Contact Us to Implement EMV Kernels in Your Business.
FAQ
An EMV Kernel is software in payment terminals that handles communication between chip cards and terminals, ensuring secure and compliant transactions.
EMV Contact Kernel requires card insertion for a secure connection. EMV Contactless Kernel uses RFID or NFC, allowing cards to be tapped or waved for faster transactions.
It’s used in retail POS terminals, ATMs, and secure environments where physical card insertion enhances security.
It speeds up transactions and enhances convenience by allowing customers to tap their cards, reducing wait times and streamlining checkout.
They use RFID or NFC technology, providing quick, tap-and-go payments, reducing wear on cards and terminals, and enhancing security.
This is a security function in the EMV Kernel that evaluates whether a transaction should proceed offline or be sent to the acquirer for online authorization based on transaction limits, terminal capabilities, and card rules.
ODA is a method used by the EMV Kernel to verify that the card is genuine and not counterfeit, using cryptographic methods like SDA (Static), DDA (Dynamic), or CDA (Combined Data Authentication).
It ensures that the EMV Kernel does not rely on specific hardware configurations. This makes the kernel reusable across various terminal devices, saving development time and cost.
EMVCo provides Level 2 certification for EMV Kernels. Card schemes like Visa, Mastercard, and others may require additional testing under their brand-specific programs.
Yes, but only within the boundaries allowed by EMVCo. Any modifications must not violate EMV logic and should still pass certification and functional testing for each card scheme.
- Level 3: Terminal Application Layer
- Level 2: EMV Kernel
- Level 1.5: Card Reader Driver or Hardware Abstraction Layer
- Level 1: Physical and Communication Layer (ISO/IEC 7816 or 14443)
The EMV Kernel (Level 2) sits between the terminal application (Level 3) and the hardware interface (Level 1). This position allows it to act as the bridge that securely manages communication between the smart card and the terminal software.
The Terminal Application Layer handles user interaction, transaction control, and communication with the acquirer. It initiates transactions, interacts with the EMV Kernel, and processes results for final approval or decline.
While the Terminal Application manages the overall flow of the transaction, the EMV Kernel is responsible for performing EMV-specific operations such as Application Selection, Cardholder Verification, Risk Management, and Authorization as per card scheme rules.
This layer abstracts the hardware details from the kernel, offering a standard interface for communication. It enables portability of the EMV Kernel across various hardware platforms without rewriting EMV logic.
- Contact Cards: ISO/IEC 7816
- Contactless Cards: ISO/IEC 14443
These standards define the physical, electrical, and data communication specifications between the card and the reader.
The EMV Kernel performs cryptographic operations, authenticates cards, verifies the cardholder, and decides if a transaction should be processed online or offline, ensuring security and reducing fraud.
Yes, modern terminals can host multiple EMV kernels (Visa, Mastercard, RuPay, etc.) to support multi-brand card acceptance. Each kernel must be independently certified.
Application Selection is the process where the terminal and card agree on which application to use from a list of supported options (e.g., Visa Debit, Mastercard Credit) stored on the card.
Cardholder Verification determines how the cardholder proves their identity (PIN, signature, or no verification). The card and terminal negotiate this using Cardholder Verification Methods (CVMs) defined in the EMV Kernel.










